NordVPN Review
We reveal why NordVPN is the #1 selling VPN service trusted by professionals and everyday users. We describe the secret sauce that’s made it a best seller in this review.


We reveal why NordVPN is the #1 selling VPN service trusted by professionals and everyday users. We describe the secret sauce that’s made it a best seller in this review.


NordVPN, based in Panama, solves one of the most notable issues with commercial VPN service providers and then adds a long list of useful features on top of that.
After years of using and reviewing dozens of VPN providers, the one issue I've always encountered is unreliability.
You could be sitting at your desk, attempting to access Hulu, only to discover that no VPN servers are available for you to use.
NordVPN servers are never down in my experience, and even in hardline countries, you can access just about any type of content without fear of being spied on by local law enforcement.
In fact, NordVPN has a vast number of other excellent features to consider. We'll go over each one one by one, so you know what to expect.

The vast majority of people who use VPN services attempt to circumvent local censorship. However, just as technology has improved to circumvent censorship, so has the technology used to enforce it.
As a consequence, unlike in the past, a standard VPN service is no longer sufficient. Those who live in Iran and North Korea, for example, can no longer rely on subpar VPN services.
Furthermore, an obfuscated server is important because it cannot be traced and blocked by the censorship team in your country, unlike a regular server.
The connection it establishes is more secure than a traditional VPN tunnel because it's nearly impossible to determine the server's or the person connecting to its IP address.
The most notable benefit is that it does not raise suspicion among ISPs that a user is connected to the internet via a VPN, which is good news in countries where VPN use is prohibited. The fact that censorship is getting worse makes a VPN even more helpful now.
Want to watch the latest Netflix shows, watch Hulu TV, and download a few Amazon Prime classics? With NordVPN's SmartPlay feature, you can watch over 150 streaming services that are otherwise unavailable in your country.
Plus, you won't notice the otherwise noticeable slowdown as much as you would without it because of smart optimization. As a result, there will be fewer loading screens, virtually no lag, and improved audio quality for all users.
NordVPN is constantly expanding its VPN server network. They currently have over 5250 servers spread across 60 countries.
Users can benefit from having servers in a growing number of countries because they can jump from one to the next to find the best connection speed and usability. It also ensures that a server is always available regardless of the circumstances.
NordVPN was one of the first VPN providers to offer encrypted proxy extensions. Unfortunately, these extensions are only available for Chrome, Edge, and Firefox for the time being.
They assist by encrypting all data you send to the proxy server, making it even more difficult for hackers and the government to intercept it. However, only the content you access through your web browser is routed through the proxy; everything else works as it would if you weren't using a VPN or proxy.
You don't need to use a separate ad blocker any longer. Adblockers, in my experience, are hit-or-miss, which means that they aren't always accurate.
Though CyberSec's new feature protects you from dangerous websites and prevents annoying advertisements from appearing, it is not without flaws.
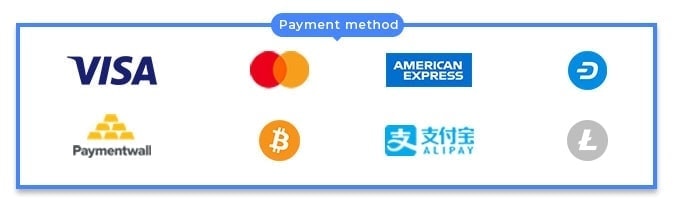
NordVPN subscriptions can be paid with Mastercard and Visa credit cards, PayPal, Paymentwall, and Bitcoin, among other methods.
More payment methods are being added to make it easier for users worldwide.
My review would be incomplete if I didn't mention their outstanding customer service. Though I've yet to have a legitimate reason to contact support, I've had a great experience calling them.
Neither during our live chat session on the chat support nor when I called the service I was put on hold. Furthermore, they dealt with all of my concerns in a professional manner.
Customer service representatives are available 24 hours a day, 7 days a week, so getting in touch with them is simple no matter where you are. Their email support is also very responsive; in our case, they responded in less than 24 hours.
NordVPN offers a Chrome extension that makes it easy for you to protect your data and hide your IP address from third parties whenever you're surfing on public Wi-Fi hotspots.
You can secure your traffic by easily connecting to your Quick Connect server of choice in just a few minutes. They have built an extensive network with cutting-edge servers that guarantee uninterrupted service alongside top security protocols.
The best thing about this extension is that it's effortless to use – once installed, all you need to do is pick a quick connect server of your choice and surf the web in peace and quiet.
NordVPN offers a Chrome extension that makes it easy for you to protect your data and hide your IP address from third parties whenever you're surfing on public Wi-Fi hotspots.
You can secure your traffic by easily connecting to your Quick Connect server of choice in just a few minutes. They have built an extensive network with cutting-edge servers that guarantee uninterrupted service alongside top security protocols.
The best thing about this extension is that it's effortless to use – once installed, all you need to do is pick a quick connect server of your choice and surf the web in peace and quiet.
In general, it depends on what you're using a VPN for. However, most companies are aware of the need for privacy and security in today's world and use a VPN as a standard practice. This can be anything from protecting company data to circumventing censorship in certain countries, or even if you want your ISP not to know that torrenting is something you do with your time instead of working. So, my answer to this would be yes, if you care about your privacy.
VPNs have no more risks than giving an online store your credit card number or having your car fixed by a mechanic who may have tampered with it. Any transaction involving trust carries the risk of money being stolen from the consumer's bank account, identity being compromised, and other undesirable outcomes. The same security principles apply to a VPN provider as they do to a website administrator or a mechanic.
With the help of a virtual private network (VPN), you can ensure that all of your online activity - including browsing history, location data, credit card numbers, and other sensitive information - is kept private from third-party websites, internet service providers, and even governments. Plus, you'll be able to prevent having your IP leaked and being ddosed online.
My experiences with paid VPN services have been varied. I use NordVPN because I frequently travel to places with restricted internet access. The service works as expected and requires no additional knowledge from you.
It also automatically blocks ads and dangerous websites, which I liked. Finally, aside from changing your IP address and remaining anonymous online via your browser, NordVPN's encrypted proxy add-on is surprisingly helpful.
All of these features, as well as others, lead me to recommend NordVPN to anyone. We also wrote a comprehensive NordVPN walkthrough guide, which we strongly advise you to read if you are new to the service.